The Government Accountability Office (GAO) released its biannual Federal Information Technology Acquisition Reform Act (FITARA) 5.0 scorecard on November 14, 2017. I wrote a detailed blog in July about the FITARA 4.0 scorecard. And now we get a chance to see the progress since this summer.
For those unfamiliar, FITARA grades executive agencies based on their implementation of Chief Information Officer (CIO) authorities, risk management, data center optimization and other factors. Now, FITARA 5.0 also measures agency ability to effectively manage software licensing, as mandated by the Making Electronic Government Accountable By Yielding Tangible Efficiencies (MEGABYTE) Act.
The FITARA 5.0 scorecard reveals that far more needs to be done specific to MEGABYTE. Of the 24 agencies covered by FITARA, 17 agencies received failing grades for their ability to manage software licensing effectively, one received a C, and the remaining six received A grades.
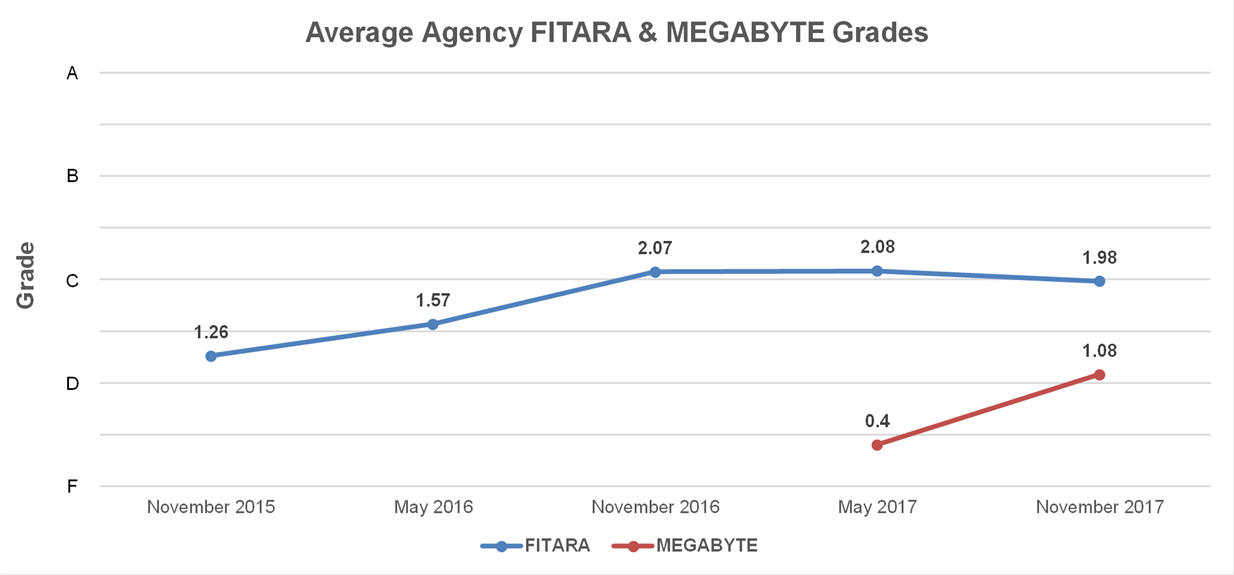
When looking at the FITARA 5.0 scorecard, one see’s far too many F grades, specific to software licensing. The fact that 17 agencies received an F for MEGABYTE confirms that these agencies are unable to baseline their license inventories and thus are likely overspending on software and remaining vulnerable to cyber threats from unmanaged assets. The scores here are perhaps not unlike for-profit organizations – struggling with many of the same challenges.
How do agencies move forward (and improve their grades)?
The prescription for improvement hasn’t changed, as I wrote in July. Implementing the provisions of the MEGABYTE act takes discipline.
The MEGABYTE Act requires the CIO of each Executive Department to achieve the following four (4) directives specific to software license management:
- Policy: Develop a comprehensive software licensing policy identifying roles and responsibilities for management
- Inventory: Establish a comprehensive inventory of software licenses (including 80% of spending and license agreements) using automated tools
- Analyze: Analyze software usage, provide training, establish goals and objectives, and implement effective decision-making using the software license management lifecycle
- Report: Send to the Office of Management and Budget (OMB), a report displaying the financial savings or avoidance of spending that resulted from improved software license management.
The risk of delaying commitment to SLM includes:
- Paying for software that is not used, or paying too much for software
- Do you know if your deployment and usage match your purchase?
- Having unsecured software deployed
- Ask anyone impacted by Petya or WannaCry – malware is disruptive to the mission, resulting in a reactive security, opposed to proactive optimization.
- Prolonged non-compliance and poor FITARA/MEGABYTE scores
- Let’s face it; nobody likes having somebody look over your shoulder. SLM, when properly implemented, makes data calls and policy compliance routine functions. You can then focus on serving agency customers, and improving performance.
